No2. Migration from External Authentication Infrastructure (with Using Directory Sync)
You are to migrate the authentication infrastructure to the IIJ ID Service in a state where you are using an external authentication infrastructure.
You are also to synchronize accounts from Active Directory to IIJ ID using Directory Sync.
[ Reference ]
The descriptions shown below are just reference.
Perform the actual task in accordance with your environment.
Federation Image
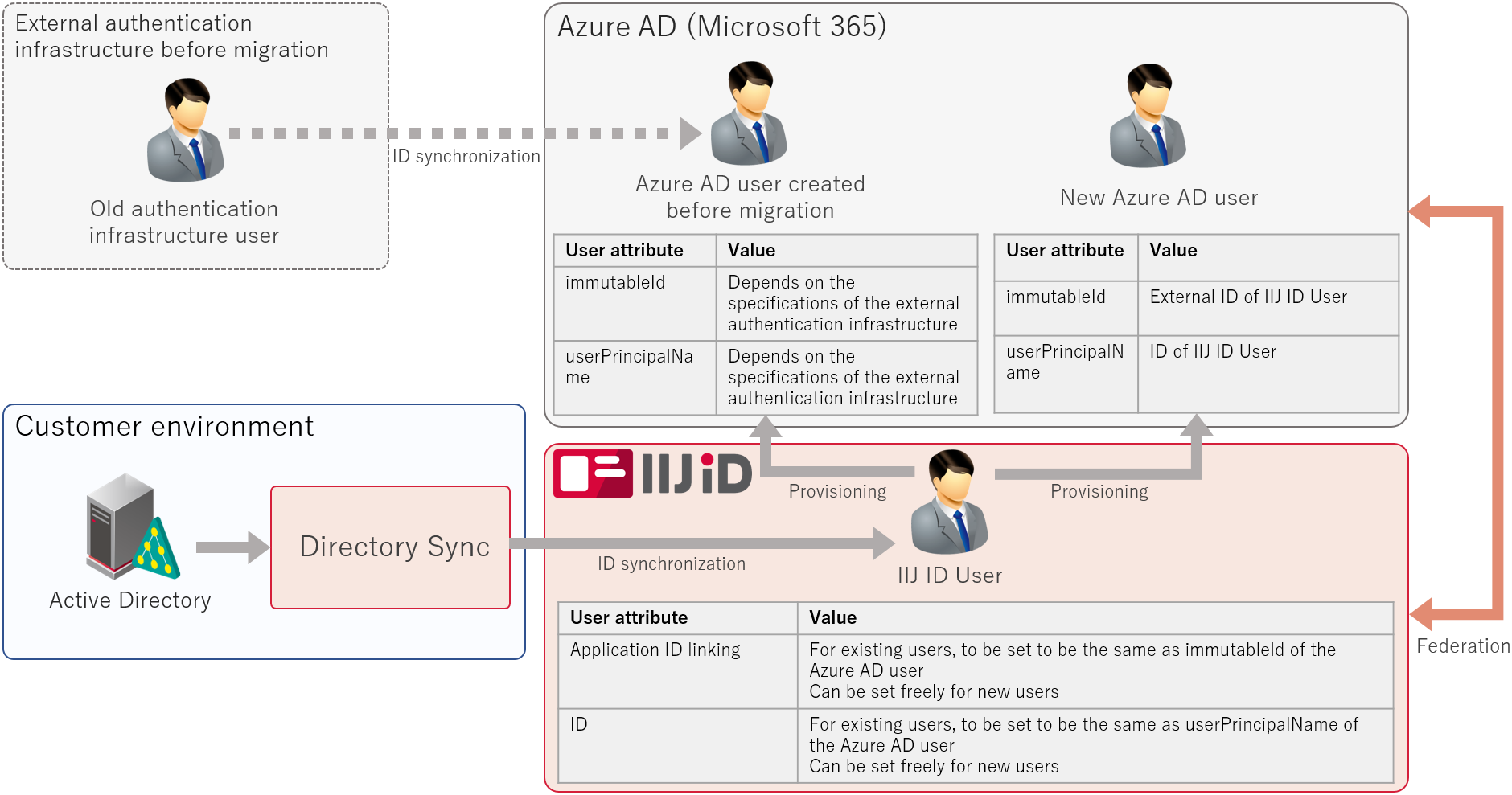
Synchronize the user by Directory Sync from Active Directory to IIJ ID.
In addition, perform provisioning on the user from IIJ ID to Azure AD, and then perform federation with the provisioned user.
Because the Azure AD user, which was created in the old authentication infrastructure, exists on Azure AD, consider the federation with the existing Azure AD user.
The value of immutableId of the existing Azure AD user depends on the specifications of the authentication infrastructure, so check it in advance.
Set the immutableId value to "any AD attribute" of the Active Directory user, so that it will be set to the external IIJ ID User ID by Directory Sync.
No value is set to the previously-mentioned "any AD attribute" for Active Directory users to be created newly. Set another Active Directory attribute (for example, objectGUID) to the application-linking ID for IIJ ID by using Directory Sync.
Setup Flow Example
| 1. Preparation | ||
|---|---|---|
| 1.1 Registering Domains in Microsoft 365 | ||
| 1.2 Configuring Windows PowerShell | ||
| 1.3 Add Microsoft 365 Application | ||
| 2. Configuring Directory Sync | ||
| 2.1 Directory Sync Setup | ||
| 3. Configuring Federations | ||
| 3.1 Changing General Application Settings | ||
| 3.2 Configuring Graph API Settings | ||
| 3.3 Provisioning | ||
| 3.4 Configuring Users | ||
| 3.5 Configuring Federations | ||
Example Configuration of Directory Sync
Perform synchronization as follows.
[ Reference ]
In this example, immutableId of the existing Azure AD user must be set to anyADAttribute (any AD attribute) or mS-DS-ConsistencyGuid of the Active Directory user.
| Active Directory | IIJ ID | Azure AD | Comments | ||
|---|---|---|---|---|---|
anyADAttribute |
-> | Application-linking ID (downstreamId) | -> | immutalbeId | The value of ms-DS-ConsistencyGuid is reflected when the value of anyADAttribute is empty. Moreover, the value of objectGUID is reflected when the value of ms-DS-ConsistencyGuid is empty. |
| userPrincipalName | -> | ID (userName) | -> | userPrincipalName |
config.yml sample
log: |
loglevel: info |
ad: |
ldap: |
server: |
addresses: |
- 127.0.0.1 |
user: 'CN=administrator,CN=Users,DC=example,DC=jp' |
base_dn: 'DC=example,DC=jp' |
filter: |
user: 'memberOf:1.2.840.113556.1.4.1941:=CN=IID_IDaaS利用者グループ,OU=IID_Groups,DC=example,DC=jp' |
group: 'memberOf:1.2.840.113556.1.4.1941:=CN=IID_IDaaS利用者グループ,OU=IID_Groups,DC=example,DC=jp' |
iid: |
scim: |
attribute: |
user: |
default: |
emails: |
- primary: true |
ad_bind: |
externalId: userPrincipalName |
downstreamId: |
- mS-DS-ConsistencyGuid |
- objectGUID |
userName: userPrincipalName |
emails: |
- value: mail |
group: |
ad_bind: |
externalId: objectGUID |
displayName: name |